A supply chain attack by the notorious REvil ransomware gang has locked up the systems of hundreds of organisations in one fell swoop after a malicious update was pushed out to customers of IT management software firm Kaseya on Friday.
The hackers appear to have gained access to the servers for Kaseya’s popular VSA platform and injected a copy of the REvil ransomware into an automatic update that was delivered to Kaseya customers over the weekend.
VSA is used by 40,000 mostly managed service providers (MSP) to manage client systems. By design, VSA has administrator rights to client systems in order to do things like deploy software and automate tasks – meaning it has a high level of trust on customer devices.
We’ve received plenty of questions about Kaseya already. In this article, we put some of these questions together and answered them to give you the information you need.
If you’ve been affected, contact us here to see how we can support.

What is Kaseya VSA?
Kaseya is a cybersecurity company offering automation software and remote management software.
Kaseya based in Dublin, Ireland, has it’s U.S. headquarters in Miami.
VSA (Virtual System Administrator) is the system tool product that has been breached to distribute the ransomware.
What is the type of attack?
This is a supply chain attack, similar in some ways to SolarWinds but with ransomware involved.
Who is responsible?
Most cyber researchers and indications are pointing to the REvil gang, a major Russian-speaking ransomware syndicate. They appear to have infiltrated the network-management package to spread the ransomware. The group has been active since April 2019 and provides, Ransomware-As-A-Service (RAAS).
This is the same group of actors blamed by the FBI for paralysing meat packer JBS last month who paid US$11 million ransom to the hacking group to decrypt their files.

When was the earliest release?
The attack appears to be timed just before the July 4 Independence Day weekend holiday.
This is a common technique; Gridware has seen a spike in attacks just before long weekends and holiday breaks where the attack is not discovered until workers return from holidays.
Who is affected or at risk?
Kaseya’s website says it has a presence in over 10 countries and more than 10,000 customers.
However, Cybersecurity firm ESET says there are victims in least 17 countries as they have MSP customers who manage many individual organisations.
In Sweden, the 800 strong grocery chain Coop’s 800 stores were unable to open because their cash registers weren’t working. The Swedish State Railways and a major local pharmacy chain were also affected.
In Germany, an unnamed IT services company told authorities several thousand of its customers were compromised, the news agency dpa reported. Also among reported victims were two big Dutch IT services companies — VelzArt and Hoppenbrouwer Techniek.
The zero-day vulnerability used to breach on-premise Kaseya VSA servers was in the process of being fixed, just as the REvil ransomware gang used it to perform a massive Friday attack.
The vulnerability had been previously disclosed to Kaseya by security researchers from the Dutch Institute for Vulnerability Disclosure (DIVD), and Kaseya was validating the patch before they rolled it out to customers.
The zero-day Kaseya vulnerability was discovered by DIVD researcher Wietse Boonstra and was assigned the CVE-2021-30116 identifier.
Cyber Researcher Fabio Viggiani @ @fabio_viggiani has identified an IP address used in the exploit: 161[.]35.239.148 User-Agent: curl/7.69.1 and described part of the attack.
The attacks commences with the deletion of logs in multiple locations and intrusion detection systems disabled and disables some features of Windows Defender.
When executed, agent.exe will drop two additional files: MsMpEng.exe (a legitimate version of the Windows Defender binary) and mpsvc.dll (REvil ransomware). The execution of MsMpEng.exe triggers the loading of mpsvc.dll (side-loading execution) and therefore executes the REvil ransomware in the context of MsMpEng.exe.
Indicators of Compromise IOCs
161[.]35.239.148
mpsvc.dll 8DD620D9AEB35960BB766458C8890EDE987C33D239CF730F93FE49D90AE759DD
agent.exe D55F983C994CAA160EC63A59F6B4250FE67FB3E8C43A388AEC60A4A6978E9F1E
agent.crt 45AEBD60E3C4ED8D3285907F5BF6C71B3B60A9BCB7C34E246C20410CF678FC0C
What is the expected cost?
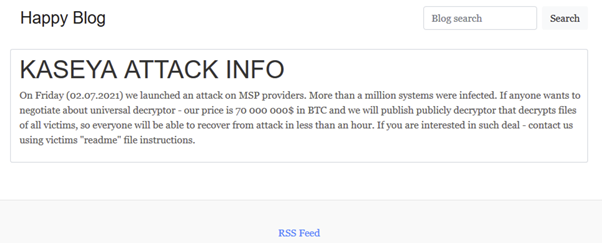
Initially, victims appeared to be getting ransoms set at US$45,000. However the REvil group appear to now offer decryption for all victims of the Kaseya attack in exchange for US$70 million (image below).
Is exfiltration involved?
The REvil gang is among ransomware gangs that steal data from targets before activating the ransomware, strengthening their extortion efforts.

What is the current containment advice?
Current advice is to shutdown VSA servers immediately and wait for patching from Kaseya.
Kaseya said it sent a detection tool to nearly 900 customers on Saturday night. Customers who experienced ransomware and receive communication from the attackers should be cautious to not click on any links as they may be malicious.
What has the U.S. President said?
When asked about the attack during a trip to Michigan on Saturday, US President Joe Biden said he had asked the intelligence community for a “deep dive” on what happened and expected to know more by Sunday.




