Known as LockBit, the ransomware gang is claiming responsibility for hacking IT giant Entrust and leaking their files.
Entrust Corp. provides software and hardware used for banking and financial transactions, e-passport production, user authentication, trust certificates, mobile credentials, and connected devices.
LockBit claims responsibility for breach
Security researcher Dominic Alvieri reported that LockBit published an Entrust data publication page on their leak site and threatened to expose all stolen information the following night.
The ransomware group attacked Entrust after purchasing access to the corporate network through “network access sellers.”
LockBit’s Entrust leak page
LockBit’s threat to make all data public insinuates Entrust has not engaged or is unwilling to comply with LockBit’s demands.
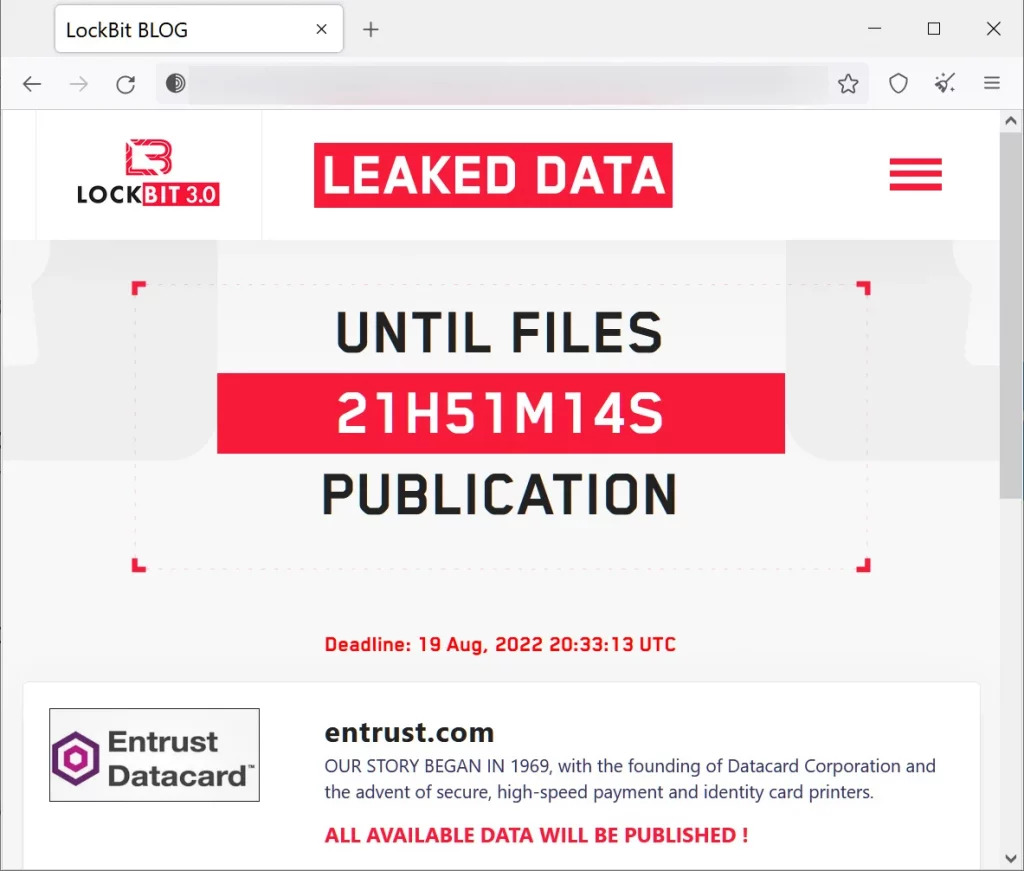
Source: SOCRadar
What has been leaked so far?
LockBit began revealing Entrust’s stolen data on August 9. Initially, screenshots were leaked that hinted at what would be next exposed.
Alvieri, who has been monitoring the breach, said accounting and legal files, as well as marketing spreadsheets, were exposed.
Entrust’s customers include a range of US government agencies, including the Department of Homeland Security, the Treasury Department, and the Department of Energy. It also includes insurance and financial companies as well as tech firms like VMware and Microsoft.
DDoS attack against LockBit
DDoS campaigns are designed to disrupt the normal operations of a website by overwhelming it with a flood of internet traffic or messages.
The LockBit sites went offline after the data began leaking. Ransomware actors claimed the attack was a DDoS attack related to their dispute with Entrust.
While the perpetrators of the DDoS attack remain unknown, a LockBit member told Bleeping Computer that the attack “began immediately after the publication of data and negotiations”.
He also separately told malware research group VX-Underground that he believed the attack was launched by someone connected to Entrust, referencing junk internet traffic that said “DELETE_ENTRUSTCOM_MOTHERFUCKERS.”
How to mitigate a privilege access attack
Experts in security and network maintenance are advised to stay informed of threat actors’ developments and tactics, as well as monitor software and firmware updates.
Reviewing accounts and privileges can significantly reduce risk of attacks, by removing accounts or privileges that are no longer needed. Make sure all digital assets are visible by implementing security measures and establishing a specialised SOC Management team. Make sure you have a backup plan in case of cyber-attacks, including ransomware.




