What Your Keyboard Tells About You
The digital world is ever evolving. One of its latest discoveries is the New Acoustic Cyber-Attack. This method can figure out 95% of what you’re typing just by listening to your keystrokes.
The Discovery: How It Works
Researchers found an interesting gap in our security. Every time we press a key on our keyboard, it makes a sound. These sounds aren’t all the same. By recording these sounds with a regular smartphone, and then feeding this information into a computer program, they managed to match the sounds to the keys with a 95% success rate.
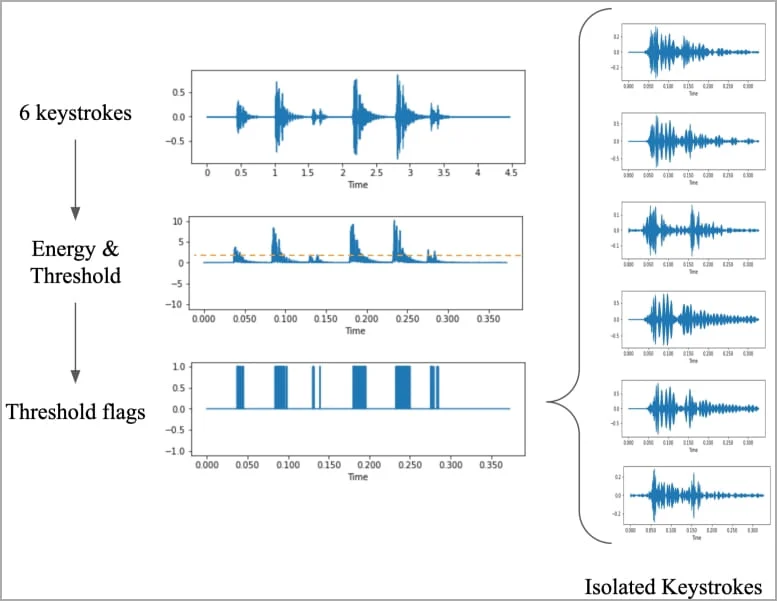
Why This Matters
Think of how often we type: emails, passwords, and personal messages. Now imagine someone being able to know what you’re writing, just by hearing your keyboard. That’s what this attack does. It listens, learns, and then knows what you’re typing.
Australia and Digital Safety
Australia’s heavy use of digital devices means we should be aware of such threats. Even if this is a new method, as more people learn about it, there’s a chance it could be used more often. But by knowing about it and taking steps, we can keep our information safe.
For those who want a deeper dive into how to stay safe, our Cyber Security Guide is the perfect resource. It’s tailored for Aussies and covers everything you need to know.
Keeping Your Keystrokes Secure
For Everyone:
While the current risk of this kind of attack is limited, these steps are particularly useful if we see an increase in similar techniques.
- Stay Informed: Awareness is your first line of defence.
- Limit Open Mic Access: Ensure apps on your device don’t have unnecessary microphone permissions.
- Background Noise: A bit of ambient noise, like music, can disrupt the clarity of keystrokes.
For Businesses:
- Educate Employees: Make them aware of potential threats with Cyber Awareness Training.
- Secure Meeting Rooms: Ensure discussions involving sensitive information are held in noise-controlled environments.
- Penetration Testing: Find and remediate vulnerabilities before they’re exploited by threat actors.




